Abstract:
IBM Guardium Vulnerability Assessment is a key part of the Guardium Database Security portfolio. It is designed to help harden database infrastructures by scanning targeted systems on a scheduled basis to detect vulnerabilities. This article explains what IBM Guardium Vulnerability Assessment (VA) actually delivers and what the differences are between the various editions. Note that since the introduction of Guardium 10, there are no longer different editions of this product and all of the Advanced Edition features are available with the product.
Content:
What is a “vulnerability assessment”?
IBM Guardium Vulnerability Assessment is a key part of the Guardium Database Security portfolio. It is designed to help harden database infrastructures by scanning targeted systems on a scheduled basis to detect vulnerabilities and risks, automate compliance and harden data environments. These scans use industry standard testing bodies (CIS, STIG, CVE), who actively seek out and publish vulnerabilities. Their purpose is simple; to identify potential threats to your data’s security and providing clear reports and recommendations for managing these vulnerabilities, supplying ammunition to fight back on today’s cyber security battlefield.
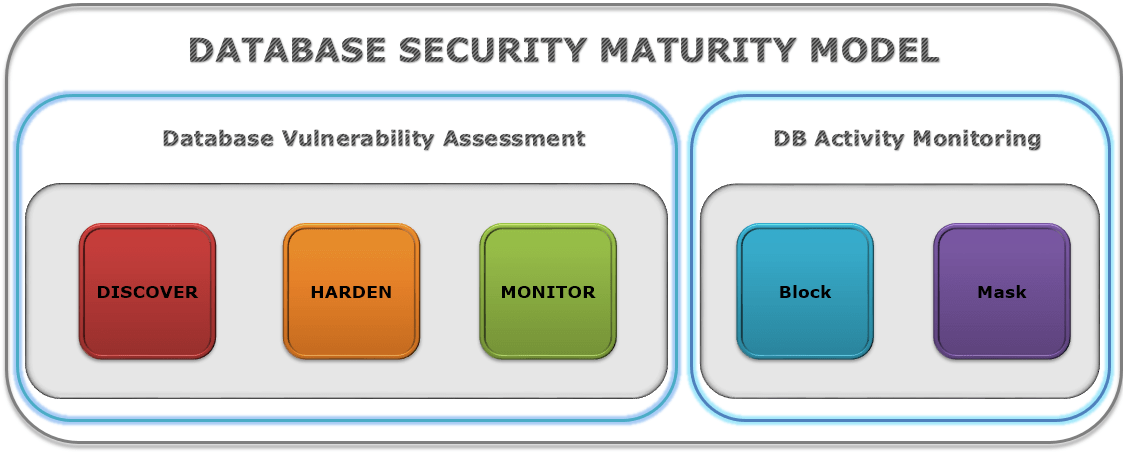
The following infographics shows the broader security spectrum, and which parts of the broader issue Vulnerability Assessment addresses.
What does a Guardium VA report look like?
The vulnerability assessment is split and reported on into the following categories:
- Privilege
- Authentication
- Configuration
- Version/Patches
- Other vulnerabilities (Errors in log files, file ownership, file permissions etc…)
These categories contain a varying number of tests associated with them (depending on which DBMS platform is being assessed); these are then broken down into severity classes as follows:
- Critical
- Major
- Minor
- Caution
- Info
Lastly, each test is then scored with the following possible results:
- Pass
- Fail
- Error
- N/A
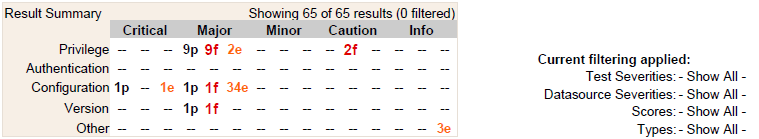
When viewing the report, a summary is provided to show the number of scored tests for each assessment categories grouped by severity – for example, we can see below that for the “Privilege” category, there were 9 passes (9p), 9 failures (9f) and 2 errors (2e) for the “Major” severity group.
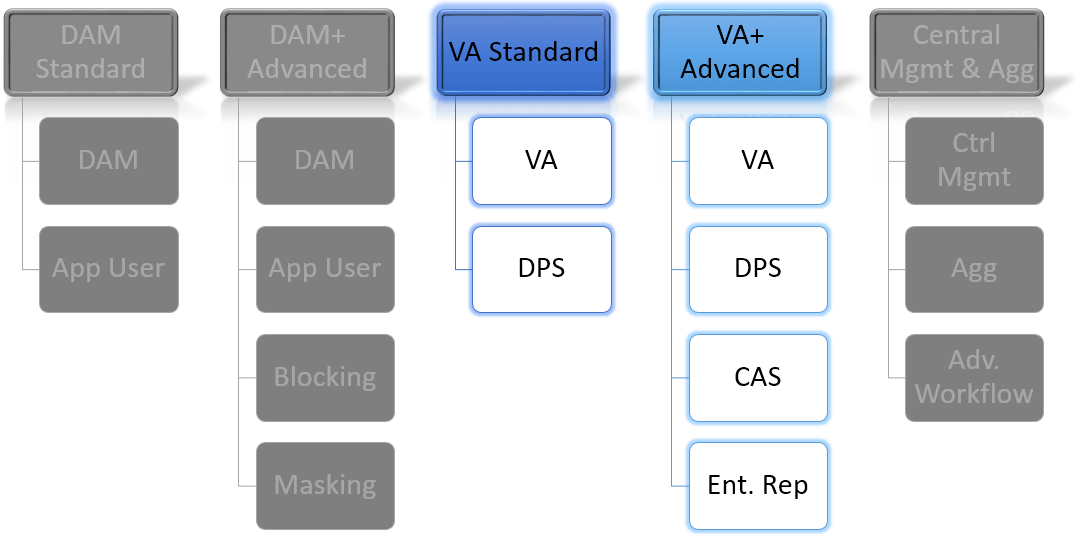
What do you get with the different editions of Guardium VA?
Prior to version 9.5, the following versions were available with Guardium VA:
- IBM Vulnerability Assessment Evaluation Edition
- IBM Vulnerability Assessment Standard Edition
- IBM Vulnerability Assessment Advanced Edition
1. “Vulnerability Assessment Evaluation Edition”
This edition is designed to provide the customer with a high-level snapshot of the current state of a database system’s security. This is a superb offering from IBM allowing a quick, free vulnerability assessment. It helps indicate whether there would be potential benefit in scheduled autonomous scans.
- It’s free.
- It allows unlimited scans for a 30 day evaluation period after which the product will cease to work.
- It doesn’t support all of the tests that the other editions support
- Like the other editions, it supports multiple database types (11 in total) including the following Informix, DB2, MySQL, Oracle, Microsoft SQL Server, Sybase and Teradata.
- Unlike the other editions, it is a complete stand-alone product consisting of a self-contained Java executable.
2. “Vulnerability Assessment Standard Edition”
Standard Edition is the first of the premium editions designed to support continuous database security vulnerability assessment. It includes the following components: VA (Vulnerability Assessment) + Database Auto-Discovery + Database Content Classifier + DPS (Database Protection Service) + Compliance Workflow Automation
- Vulnerability Assessment – performs scans of the database infrastructure for vulnerabilities and provides an evaluation of database and data security health, with real time and historical measurements presented in a digestible format to allow issues to be quickly prioritised and actioned.
- Database Auto-Discovery – performs an agent-less network scan of the database environment and creates graphical representation of interactions among database clients and servers, this is a key step in understanding where your data lies. .
- Database Content Classifier – automatically discovers and classifies sensitive data, such as 16-digit credit card numbers and 9-digit Social Security numbers, helping organisations quickly identify faulty business or IT processes that store confidential data. .
- Database Protection Service – a subscription service that provides periodic updates to vulnerability tests and other predefined content (reports, groups, policies) .
- Compliance Workflow Automation – allows automation of the entire compliance process through starting with assessment and hardening, activity monitoring to audit reporting, report distribution, and sign-off by key stakeholders.
3. “Vulnerability Assessment Advanced Edition”
Advanced Edition is the higher of the premium editions designed to support continuous database security vulnerability assessment. It includes all of the components with Standard Edition and also: CAS (Change Audit System) + Database Entitlement Reports
- Change Audit System – tracks changes and reports on them, e.g. changing configuration files, registry variables, or other DB or OS components, including executable files or scripts used by the DB or OS.
- Entitlement Reports – provide the process of validating and ensuring that users only have the privileges required to perform their duties.
Adapted from, IBM Technote, http://www-01.ibm.com/support/docview.wss?uid=swg21640182
All of the above provide strong base reports and templates out of the box, however, full customisation is supported to create personal tests, exceptions, classifications etc…
“Vulnerability Assessment (v9.5+)”
The above list is now included as a whole package under “VA”. Database Entitlement Reports is now part of the Base offering, included in both editions of DAM and the new single VA tier. There are no new features or enhancement to VA from v9.5+ (excluding the general overall product improvements and enhancements)
Conclusion:
This article has highlighted the difference between the Guardium Vulnerability Assessment offerings. With the latest edition of Guardium 10, there is a single choice of “VA” making the product offering and licensing simpler to understand. Although VA is just a piece of the overall goal to address data protection challenges, the tools it can equip an organisation with make the challenge a little more digestible.
Disclaimer:
The above is provided “as is” without warranty of any kind, either express or implied, including without limitation any implied warranties of condition, uninterrupted use, merchantability, fitness for a particular purpose, or non-infringement.
Contact us
Find out more about our vulnerability assessments. If you have any questions or would like to find out more, simply contact us.

